Password phishing is a problem, time for phish-resistant authentication now
Time to Consider Phish-Resistant Authentication
A phish attack recently was attempted on me. In a way, I am glad it happened because I can now share it with you, to help demonstrate that phishing still works because it bypasses all the former best security practices, I say former because now there are better solutions. It’s time to start taking advantage of nextgen authentication, FIDO2 and webauthn. Your customers need it, to help defeat real attacks like password phishing.
A funny thing happened on the way to my bank login last week, I got this password phishing text message below. Notice the ‘CHASE ALRET’ misspelling. Right off the bat, I know this is some kind of attack. It always amazes me how much effort an attacker goes through to get my contact info, get a hosting account, fake a login page but not use spell check. The new part about this is that I don’t normally get text message attacks, they are almost always email. I would have to guess mobile attacks are poor for phishing because it is so annoying to type a password on a mobile keyboard, but I guess the attackers are going were the volume of users are.

Onto the Investigation
The first thing I did was to check the password phishing url with the Rex Swain HTTP viewer. https://www.rexswain.com/httpview.html I use the Rex Swain HTTP viewer because I don’t want to go to the link on my browser in case it exploits some zero-day browser vulnerability, and the Rex Swain viewer gives me all the headers and content in a way that I can easily scroll and CTRL+F search.

As we can see here, the page contents perform a simple javascript redirect to another page:

Notice it is specifically designed to look close to a Chase bank URL but clearly it is on a generic domain ‘serveftp.com’.
And interestingly enough, the sleuths include Google Analytics which you would think would alert google to the maliciousness of the page. Wouldn’t it be nice if this would cause some kind of trigger at google to do a crawl and develop an opinion on the page, but that was not the case, the Google safe browsing api listed this as safe.
Now when I checked this serveftp.com link in the hand dandy Rex Swain tool I got a 404 response. That made me quite suspicious, because this would be a lot of effort just to 404, and I had a hunch the phishing page was trying to evade bots and crawlers to avoid detection. So I tried another tool called browserling https://www.browserling.com/ and sure enough, when a real browser visited the page it showed a fake Chase login screen.

They put some time into this page, compare it to the actual real Chase page. Scary close if you ask me, and quite believable.

Password Phishing Attack Confirmed
So now that I have confirmed this is an actual real phish attack, I next want to see what the scan tools think. Using VirusTotal https://virustotal.com/ I can see what the leading anti-malware and URL filtering engines think for each link.
For the first link, only 5 out of 93 think it is malicious. That is a pretty poor performance of these “best in class detectors.” If you are relying on them for protection, you are out of luck.

Now onto the second link that I confirmed was a Chase phishing page, only 2 of 95 identified this as malicious, even worse performance!

Wrapping It Up, Handing it Off to Google
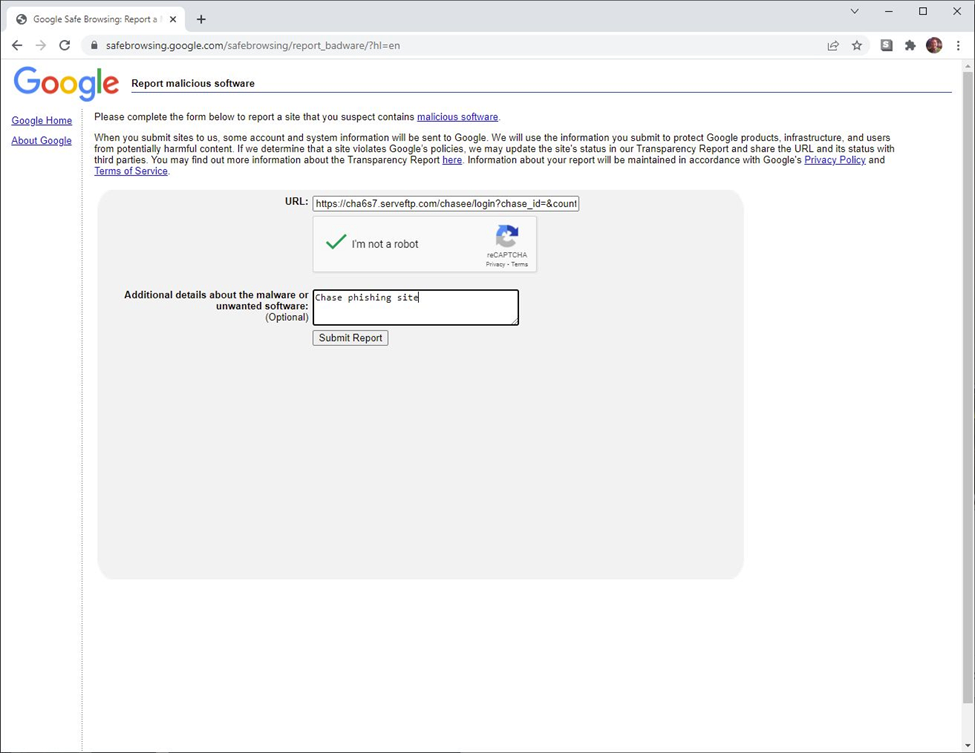
To wrap up my phishing investigation, I submit this URL to google at their safebrowsing api https://www.google.com/safebrowsing/static/submit_malware.html?hl=en and have them get the word out.
My point in sharing my real life phishing attempt is to reiterate that our passwords are under attack, and unfortunately, traditional password mitigation and protection is antiquated. It isn’t all bad news though; better authentication options are like Vault Vision is available with strong security protocols like FIDO2 and webauthn technologies. Vault Vision helps developers migrate their user authentication for increased security and eliminating passwords. Your customers deserve the strongest security that is easy to deploy and maintain.
